Overview of TeamTNT's Renewed Campaign
The infamous cryptojacking group TeamTNT has ramped up efforts in a fresh wave of attacks targeting cloud-native environments, with a primary focus on mining cryptocurrency and renting out compromised servers to third parties. This latest campaign leverages exposed Docker daemons to infiltrate cloud infrastructures, deploying crypto-miners and the Sliver malware to expand their reach and monetize hijacked computing power.
Exploiting Docker Vulnerabilities
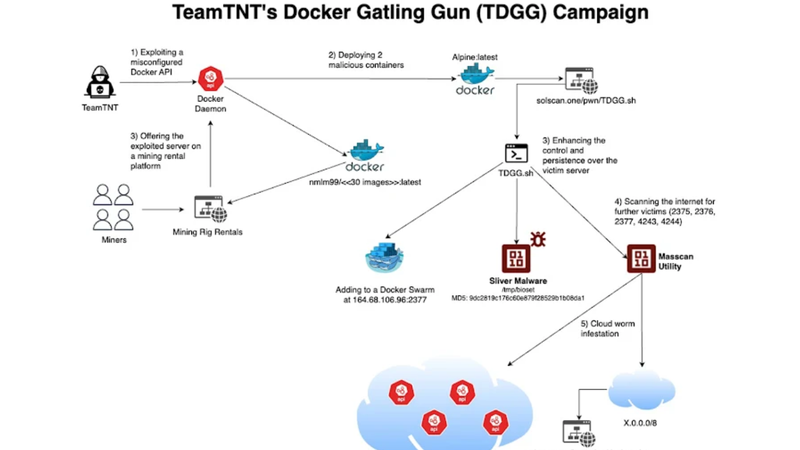
TeamTNT has identified exposed Docker API endpoints as their entry points for this operation, scanning millions of IP addresses to locate unprotected servers. Once accessed, they deploy an Alpine Linux-based container embedded with malicious code retrieved from a compromised Docker Hub account, running a shell script known as "Docker Gatling Gun" (TDGGinit.sh) to perform further exploitations.
New Tactics with Advanced Malware
A key adaptation in this campaign is the replacement of TeamTNT's previously favored Tsunami backdoor with the more advanced Sliver command-and-control (C2) framework. This shift allows TeamTNT to remotely control infected servers with improved resilience, reinforcing their capacity to conduct prolonged attacks. Aqua’s Director of Threat Intelligence, Assaf Morag, confirmed that TeamTNT also maintains signature names for C2 operations, such as “Chimaera” and “set,” suggesting a well-organized assault.
Offering Mining Capacity to Other Parties
In addition to crypto mining, TeamTNT monetizes its operations by selling access to the compromised infrastructure on rental platforms like Mining Rig Rentals. This strategy not only offloads resource management to third-party users but also highlights the evolution of their illicit business model as they diversify revenue streams from breached systems.
New Evidence and Observations from Security Experts
Aqua Security first identified this renewed campaign, noting the group’s reliance on an Anonymous DNS (anondns) to conceal the location of their web server. Datadog also provided early insights, initially detecting attempts to enlist infected Docker instances into a Docker Swarm. Though hesitant to formally attribute the attacks, Datadog's findings align with TeamTNT’s known methods.
Got a knack for writing and a knack for making money?
The Role of the Prometei Botnet
In a parallel development, Trend Micro exposed a separate but similarly dangerous campaign involving the Prometei botnet. Promote targets unprotected Remote Desktop Protocol (RDP) and Server Message Block (SMB) systems, engaging in credential theft, security evasion, and network propagation. These infected devices are subsequently linked to a Monero mining pool, quietly generating revenue without alerting system administrators.
Conclusion
As TeamTNT continues to adapt its strategies, this latest offensive underscores the need for robust cloud security measures, especially for Docker and other containerized environments.
Comments